Shadow IT: How to Find and Address Unapproved Technology in Your Organization

In today’s fast-paced digital landscape, Singaporean SMEs are under constant pressure to innovate, improve efficiency, and offer greater flexibility to their teams. However, this agility often introduces hidden risks—most notably, Shadow IT. This article will help you understand what Shadow IT is, why it’s a problem for SMEs, and provide practical guidance on how to address it without stifling your team’s productivity.
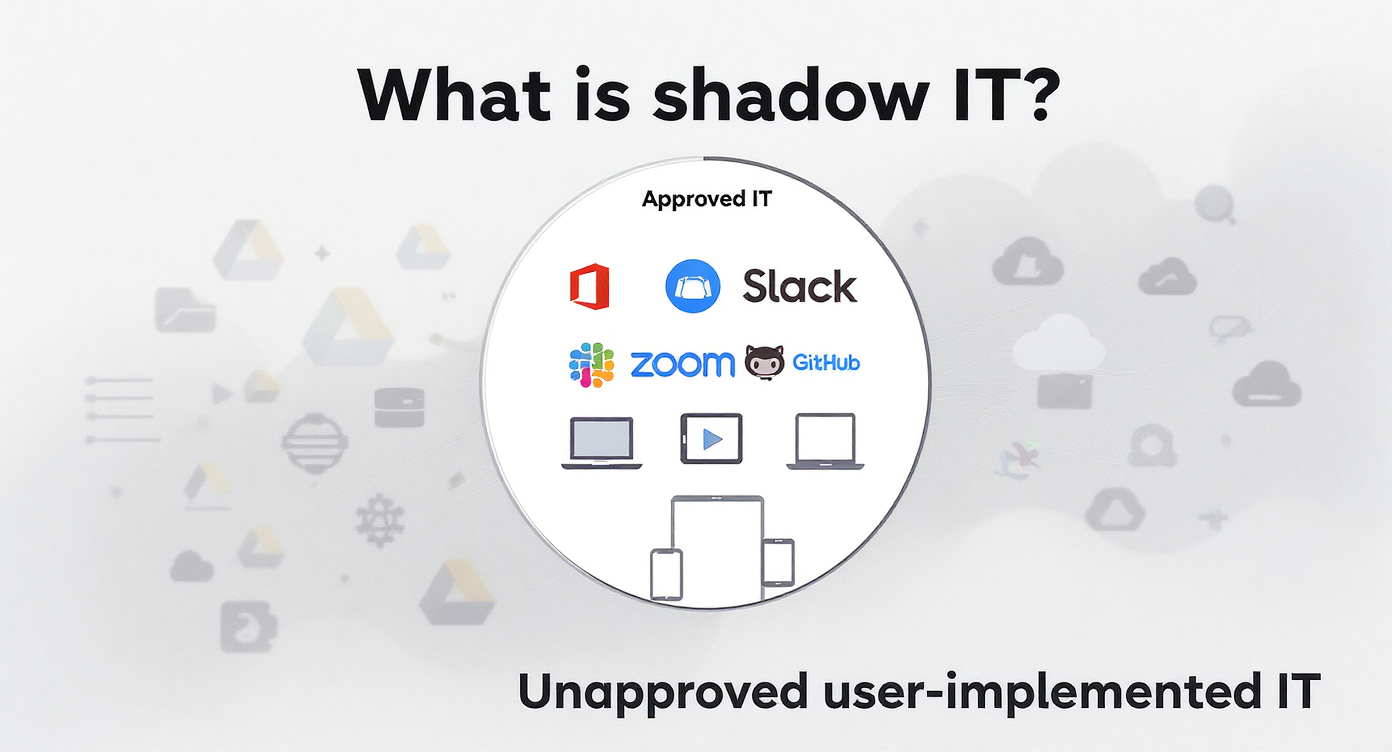
What Is Shadow IT? Common Forms in the SME Workplace
Shadow IT refers to any technology, application, device, or cloud service that employees use for work without formal approval or oversight from the organization’s IT department. While often well-intentioned, Shadow IT is usually adopted by staff seeking faster, more convenient ways to accomplish tasks outside the boundaries of official company tools or policies.
Common examples include:
- Unauthorized Software and Apps: Using free or trial versions of project management, file-sharing, or messaging tools without company approval.
- Personal Devices (BYOD): Accessing work email or sensitive company data on personal smartphones, tablets, or laptops.
- Unsanctioned Cloud Services: Creating accounts on services like Dropbox, Google Drive, or WhatsApp to share files or collaborate outside of officially approved platforms.

Why Is Shadow IT a Problem for SMEs?
While Shadow IT might appear harmless, especially in resource-constrained environments where SMEs desire “quick fixes,” it introduces several serious risks:
1. Data Breaches and Loss
Unapproved tools may lack enterprise-grade security controls, making it easier for cybercriminals to access company data. Data stored or shared via unauthorized channels may not be encrypted, secured, or backed up, increasing exposure to breaches.
2. Compliance Issues
For Singaporean SMEs bound by data protection regulations such as PDPA, Shadow IT can lead to breaches of compliance. Sensitive data could be stored in ways that don’t meet regulatory requirements, putting the business at risk of hefty penalties.
3. Operational Inefficiency
When employees use various unsanctioned apps, data is siloed, support is fragmented, and processes become inconsistent. This makes it difficult to manage information, support users, and troubleshoot issues effectively.
4. Increased IT Costs and Complexity
Hidden technology usage may result in duplicated subscriptions, unplanned support costs, and wasted resources when overlapping tools are adopted.

How to Detect and Identify Shadow IT in Your SME
Taking control of Shadow IT starts with visibility. Here’s how SMEs can discover what’s really happening:
1. Conduct IT Audits
Regularly review company devices and networks for unauthorized software or connected devices. Check operating systems for installed apps and browser histories for cloud platform logins.
2. Network Monitoring
Use network monitoring tools (even affordable, cloud-based options for SMEs) to identify unusual traffic patterns—such as frequent uploads to external file-sharing services.
3. Employee Surveys and Interviews
Engage staff with non-punitive surveys asking about the tools they use and why. Employees are often quick to share effective solutions—use this information to guide your IT strategy.
4. Review Expense Claims
Monitor business expense submissions for software or subscription expenses not previously approved by IT or management.

Strategies to Address and Mitigate Shadow IT
1. Educate Your Team
Hold periodic training sessions to raise awareness about cybersecurity (including modern frameworks like Zero Trust), data privacy, and the risks of using unapproved technology. Ensure employees understand both the “why” and the “how” of secure tech use.
2. Implement Approved Alternatives
Offer employees legitimate, easy-to-use solutions that address their pain points. When staff have access to effective collaboration tools, the temptation to adopt unsanctioned ones drops significantly.
3. Foster Open Communication
Create channels for employees to request new tools or voice frustrations about existing ones. Encourage innovation—but ensure all new tools are vetted by IT for security and compliance before adoption, and support changes with change management best practices.
4. Establish and Enforce Clear Policies
Develop comprehensive IT usage policies outlining acceptable tools, data handling expectations, and procedures for introducing new technologies. Make policy documents accessible and keep them updated as needs evolve.
5. Leverage MSP and Cloud Solutions
Consider engaging a Managed Services Provider (MSP) that offers transparent, fee-only IT management and strategic advice. Providers like Techease Solutions can help SMEs select, implement, and manage secure, scalable IT solutions tailored to their needs and budget.
Balancing Security with Productivity and Innovation
The key to managing Shadow IT isn’t rigid restriction, but thoughtful enablement. Security should protect—not hinder—business operations and growth; with the right managed IT approach, it can even accelerate innovation. Involve team leaders and users in IT decision-making, prioritize user experience when choosing tools, and reward staff for suggesting improvements or flagging security concerns.
Real-World Examples
- Shadow IT Leading to Data Leak: A local SME suffered a data breach after employees shared client files using personal Dropbox accounts, resulting in unauthorized access and unintentional PDPA violations.
- Proactive Approach Pays Off: Another SME partnered with a fee-only MSP to audit application usage, replaced rogue apps with secured cloud platforms, and implemented cyber-awareness training—halving their helpdesk load and significantly reducing compliance risk.
Next Steps for Your SME
Don’t wait for a crisis to uncover hidden technology risks.
- Review your organization’s existing IT usage policies and update them regularly.
- Initiate an internal dialogue about technology needs—encourage openness while reinforcing security’s importance.
- Consider consulting with a professional, vendor-agnostic IT partner to audit your environment, recommend best-fit tools, and support digital transformation.
Shadow IT is a reality for modern businesses, but with the right approach, you can harness your team’s innovation while protecting your SME against costly cyber risks.
Need help managing IT risks or want to review your internal technology strategy? Reach out to a trusted MSP for unbiased, transparent guidance tailored to your business growth.